Tl;dr: Search engine phishing exploits the trust we have in search engines and the convenience of searching for something rather than remembering the domain. The following piece outlines what search engine phishing attacks may look like and how Coinbase users can avoid them.
By Coinbase Security Team
How do you log in to Coinbase? If you’re like many people, you open your preferred browser and type “Coinbase” or “Coinbase login” in the address bar. You expect to get results like this:
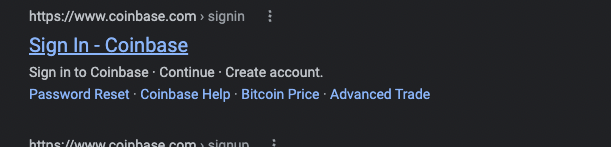
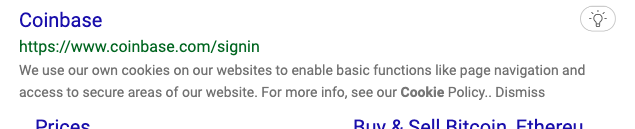
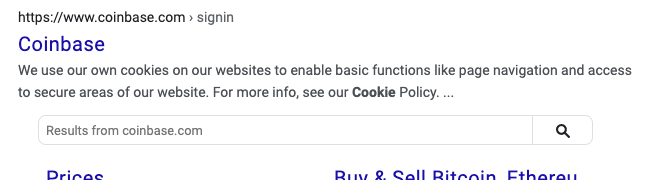
But sometimes you may get results like this:
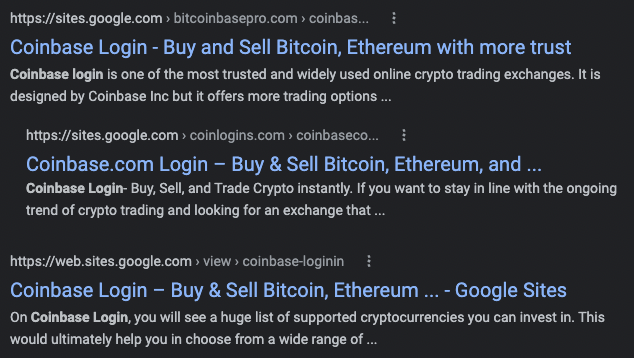
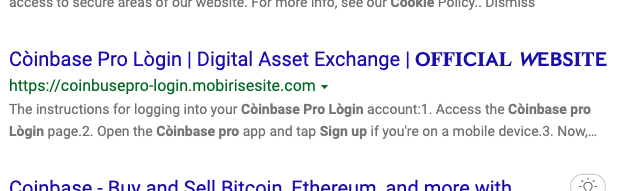
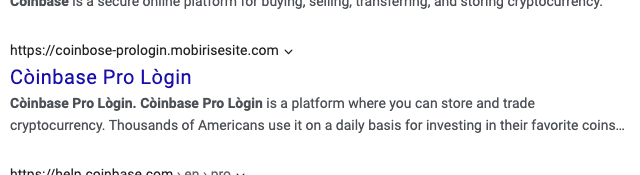
The second set of screenshots show an example of phishing links. This is called search engine phishing and it has become a trend for attackers targeting Coinbase accounts.
When most people think of phishing, email or SMS phishing comes to mind. However, phishing can take many forms. Search engine phishing exploits the trust we have in search engines and the convenience of searching for something rather than remembering the domain.
We all do it, but this opens us up to potential search engine phishing attacks if we are not diligent about checking our links and protecting ourselves online. Here are some tips to prevent this from happening to you:
Coinbase uses a uniform naming convention for our websites and pages. The convention follows this pattern: [page].coinbase.com. For example, here are some of our pages:
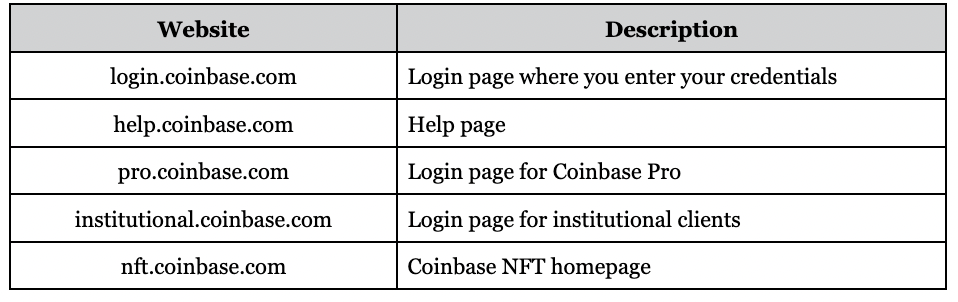
One way to avoid this type of scam is to bookmark the above Coinbase pages that you frequent. Bookmarking removes the need to search for, or manually type, a domain name. Here is a quick tutorial on how to create bookmarks in the most popular browsers.
It takes a good amount of work for anyone to get their website ranked high in search engine results. This is called Search Engine Optimization (SEO), which is the process of improving the traffic from search engines to a website. Some website services, including Google Sites and Microsoft Azure, offer built-in SEO functionality.
As seen in the screenshots above, attackers tend to exploit website services like Google Sites and Microsoft Azure — building a false sense of trust in the phishing link.. The naming conventions might follow a pattern like one of the following:
sites.google.com/[phishingpage].com
[phishingpage].azurewebsites.net
These phishing websites will typically then redirect to another phishing page after a victim clicks a button on the site. The redirect will take the victim to a second phishing page where the actual phishing attack happens. Using a second…
Click Here to Read the Full Original Article at The Coinbase Blog – Medium…
























