Soon after Thirdweb revealed a security vulnerability that could impact a variety of common smart contracts used across the Web3 ecosystem, OpenZeppelin identified two specific standards as the root cause of the threat.
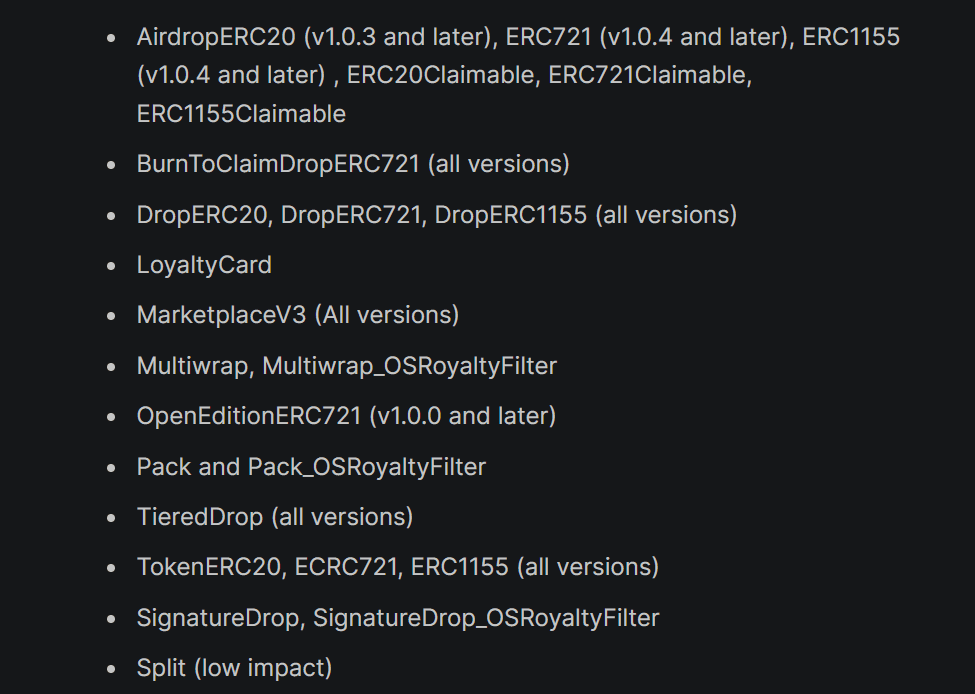
On Dec. 4, Thirdweb reported a vulnerability in a commonly used open-source library, which could impact pre-built contracts, including DropERC20, ERC721, ERC1155 (all versions), and AirdropERC20.
IMPORTANT
On November 20th, 2023 6pm PST, we became aware of a security vulnerability in a commonly used open-source library in the web3 industry.
This impacts a variety of smart contracts across the web3 ecosystem, including some of thirdweb’s pre-built smart contracts.…
— thirdweb (@thirdweb) December 5, 2023
In response, smart contracts development platform OpenZepplin and NFT marketplaces Coinbase NFT and OpenSea proactively informed users about the threat. Upon further investigation, OpenZepplin found that the vulnerability stems from “a problematic integration of two specific standards: ERC-2771 and Multicall.”
The smart contract vulnerability in question arises after the integration of ERC-2771 and Multicall standards. OpenZepplin identified 13 sets of vulnerable smart contracts, as shown below. However, crypto service providers are advised to address the issue before bad actors find a way to exploit the vulnerability.
OpenZepplin’s investigation found that the ERC-2771 standard allows the overriding of certain call functions. This could be exploited to extract the sender’s address information and spoof calls on their behalf.
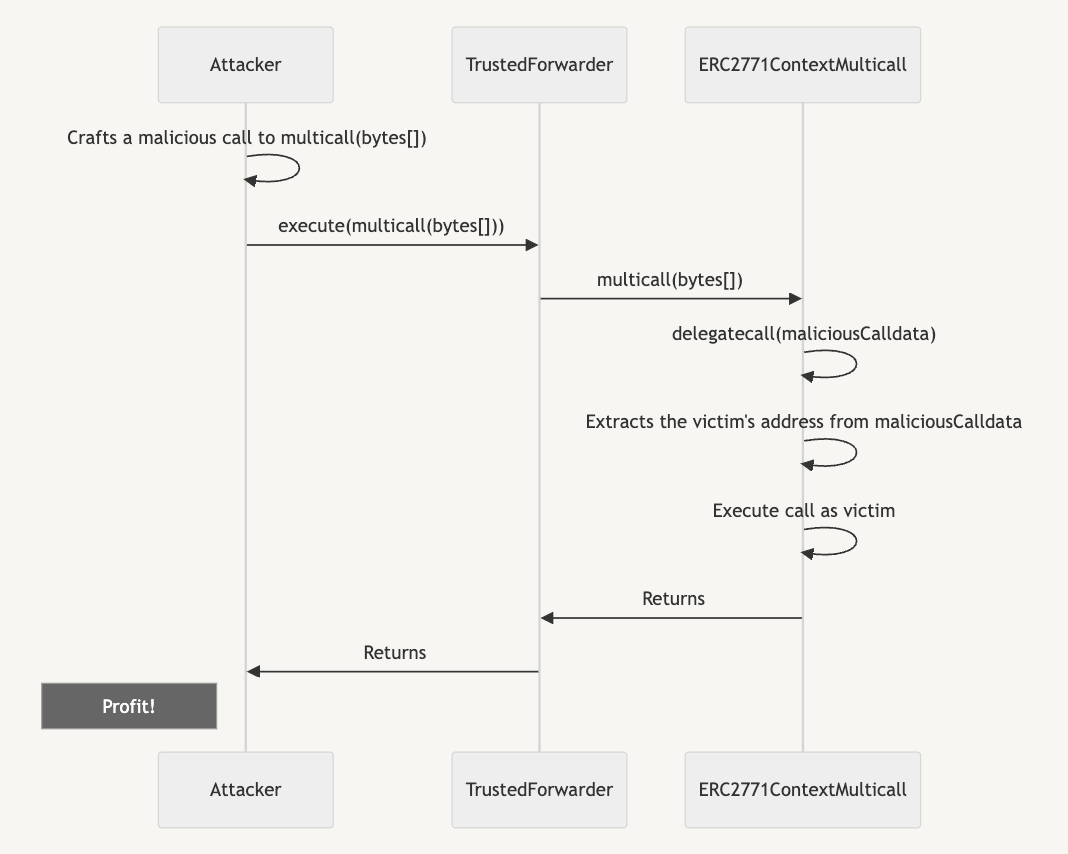
OpenZepplin advised the Web3 community using the aforementioned integrations to use a 4-step method for ensuring safety — disable every trusted forwarder, pause contract and revoke approvals, prepare an upgrade and evaluate…
Click Here to Read the Full Original Article at Cointelegraph.com News…