[the_ad id="2528"]
[ad_1]
Blockchain bridges allow decentralized finance (DeFi) users to use the same tokens across multiple blockchains. For example, a trader can use USD Coin (USDC) on the Ethereum or Solana blockchains to interact with the decentralized applications (DApps) on those networks.
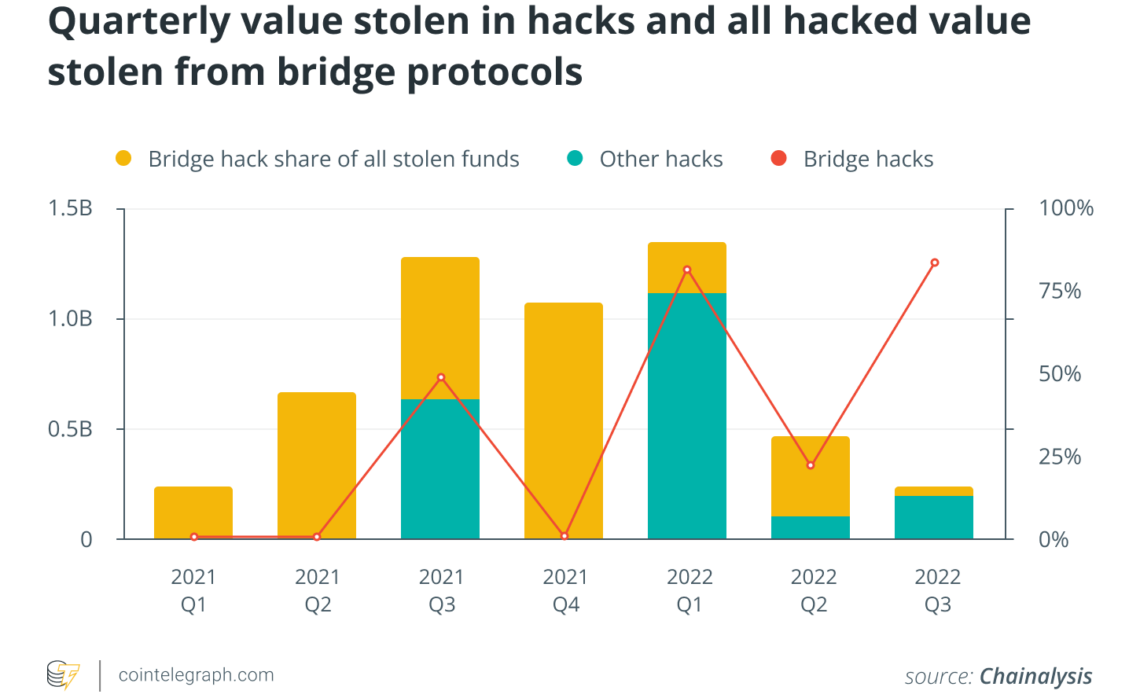
While these protocols may be convenient for DeFi users, they are at risk of exploitation by malicious actors. For example, in the past year, the Wormhole bridge — a popular cross-chain crypto bridge between Solana, Ethereum, Avalanche and others — was hacked, with attackers stealing over $321 million worth of wrapped Ethereum (wETH), the largest hack in DeFi history at the time.
Just over a month later, on March 23, 2022, the Ronin Network bridge — Axie Infinity’s Ethereum-based sidechain — was hacked for over $620 million, and on Aug. 2, the Nomad bridge was hacked for over $190 million. In total, over $2.5 billion was stolen from cross-chain bridges between 2020 and 2022.
Trustless bridges, known as noncustodial or decentralized bridges, could improve users’ security of cross-chain transfers.
What is a blockchain bridge?
A cross-chain bridge is a technology that allows sending of assets or data from one blockchain network to another. These bridges allow two or more separate blockchain networks to talk to each other and share information. The interoperability provided by cross-chain bridges makes it possible to move assets from one network to another.
Recent: SEC vs. Kraken: A one-off or opening salvo in an assault on crypto?
Most bridging technologies use smart contracts on both blockchains to make cross-chain transactions possible.
Cross-chain bridges can move many assets, such as cryptocurrencies, digital tokens and other data. Using these bridges makes it easier for different blockchain networks to work together and for users to take advantage of each network’s unique features and benefits.
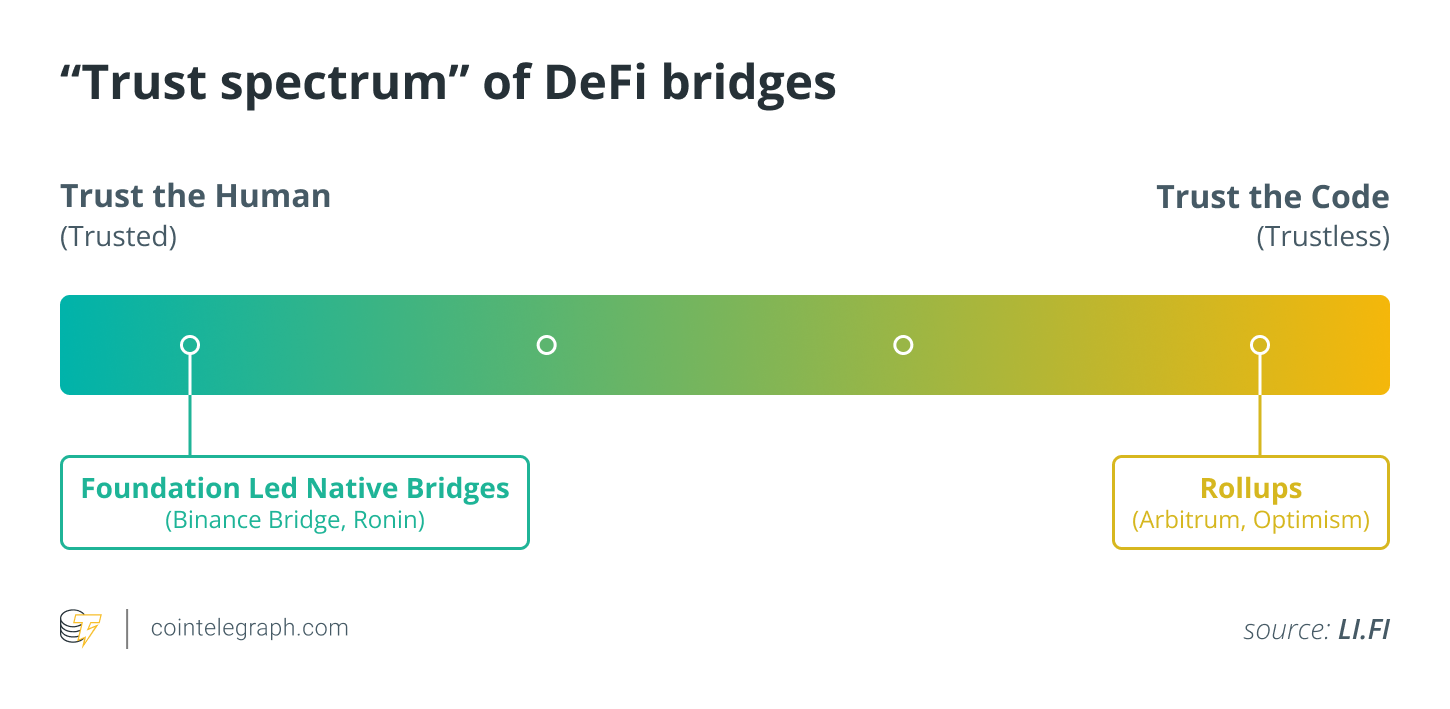
Trusted bridges vs. Trustless bridges
When it comes to bridging protocols, there are two main types, centralized (trusted) bridges and decentralized (trustless) bridges. Trusted bridges are managed by centralized entities that take custody of the tokens once they are transferred to the bridge. A major risk with custodial bridges is the single point of failure (the centralized custodian), which makes it an easier target for hacking attempts.
Instead of using centralized custodians to transfer tokens across blockchains, trustless bridges use smart contracts to complete the process.
Smart…
Click Here to Read the Full Original Article at Cointelegraph.com News…
[ad_2]